As we move deeper into 2025, companies operating in the European Union are facing more than just compliance deadlines; they’re navigating a fundamental shift in how cybersecurity and data protection are governed. Two key frameworks are leading this evolution:
- NIS2 Directive: Raising the bar for cybersecurity readiness across a wide range of sectors.
- GDPR: Still the gold standard for personal data protection, but now under review for simplification; especially for SMEs.
Together, they signal one thing: compliance isn’t optional, and operational resilience is no longer a nice-to-have; it’s essential.
NIS2 Directive: A new cybersecurity baseline for Europe
In effect since October 18, 2024, the updated Network and Information Security Directive (NIS2) expands on its 2016 predecessor by introducing stricter, clearer, and broader obligations for organizations in both essential and important sectors.
Who’s affected?
NIS2 now applies to medium and large organizations in:
- Energy, water, and transport
- Digital infrastructure and public administration
- Healthcare and pharmaceutical manufacturing
- Postal, courier, and food supply services
- Medical devices, chemicals, and semiconductor production
Thousands of organizations across the EU now fall within its scope; many for the first time.
Key changes under NIS2
- Expanded scope: Targets both essential and important entities in critical sectors. Includes additional sectors in comparison to the NIS1 directive.
- Executive responsibility: Top management is directly accountable; non-compliance could lead to personal liability.
- Tight incident reporting: Notify authorities within 24 hours of a major incident; deliver a full report within 72 hours.
- Supply Chain security: Organizations must assess and manage third-party risks, making cybersecurity a contractual priority. Which basically means that many organizations will fall, indirectly, under the NIS2 regulation.
- Serious consequences: Fines of up to €10 million or 2% of global turnover for essential entities.
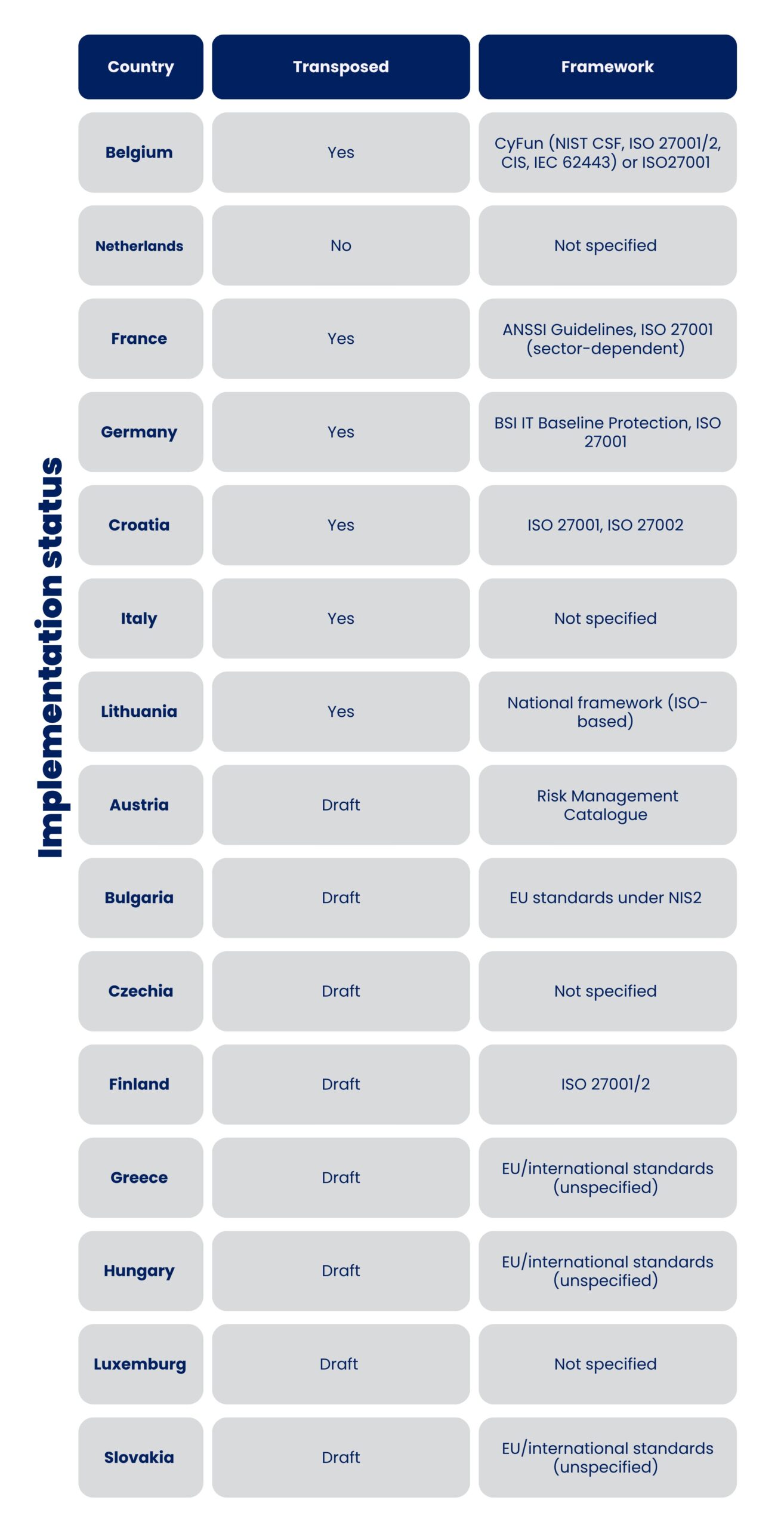
Implementation status
While the EU deadline for national adoption was October 17, 2024, progress is uneven: Belgium, Italy, Lithuania, and Croatia are ahead, while France, Spain, and Portugal are behind, leading the European Commission to start legal action against 23 Member States.
A short overview of some EU countries can be found below. If you want more detailed information, you can find more information on the website of ESCO.
ISO 27001 and CyFyn: Practical tools for NIS2 implementation
With the expanded scope of NIS2 and rising expectations for cybersecurity maturity, many organizations are turning to internationally recognized frameworks such as ISO 27001 and the CyFun framework to implement consistent, auditable security practices.
Why ISO 27001?
ISO 27001 is a globally recognized standard for information security management systems (ISMS), providing a risk-based, structured approach to protecting data and systems. It’s particularly effective for:
- Demonstrating compliance with NIS2 obligations, especially around risk management, incident response, and supply chain controls.
- Building trust with clients, regulators, and partners through third-party certification.
- Creating repeatable processes for identifying, assessing, and mitigating information security risks.
Key controls from Annex A of ISO 27001 directly map to NIS2 requirements such as access control, physical security, supplier relationships, and incident management.
What is CyFun?
CyFun (Cyber Fundamentals) is a national implementation framework used in Belgium that blends global standards—NIST CSF, ISO 27001/2, CIS Controls, and IEC 62443—into a practical, sector-neutral approach. CyFun helps organizations:
- Assess their maturity using a clear baseline with five levels of implementation.
- Prioritize actions based on their operational environment and critical dependencies.
- Integrate cybersecurity into broader governance, risk, and compliance systems.
CyFun is especially beneficial for organizations that need flexibility and scalability in their implementation efforts, and it’s recognized by Belgium’s NIS2 transposition law as a valid compliance route.
GDPR in 2025: Simplifying, not softening
Introduced in 2018, the General Data Protection Regulation (GDPR) reshaped how companies handle personal data. But over time, many organizations; especially SMEs—have struggled with its complexity and administrative burden.
What’s changing?
The European Commission is now proposing ways to reduce GDPR friction without weakening protections. Key priorities:
- Easier compliance for small and medium-sized enterprises (SMEs)
- Simplified documentation and audit processes
- More tailored guidance from national authorities
- Requirements scaled to company size and data sensitivity
These reforms aim to make GDPR more operationally realistic, especially for fast-moving, resource-constrained businesses.
Key cybersecurity and data privacy trends in 2025
As organizations align with evolving frameworks like NIS2 and GDPR, they must also recognize the broader forces shaping digital security. From AI-driven threats to the operational realities of privacy laws, these five trends are defining cybersecurity and data protection in 2025.
- AI in cybersecurity
Artificial Intelligence is transforming both offensive and defensive strategies in cybersecurity. Attackers are leveraging AI to launch more convincing phishing attacks, generate deepfakes, and deploy malware that adapts in real time. In response, defenders are turning to AI to automate incident detection and improve threat response.
According to recent CISO research, nearly nine out of ten (86%) business leaders with cybersecurity responsibilities reported experiencing at least one AI-related incident in the past 12 months.
- Ransomware and supply chain
Ransomware attacks are becoming more aggressive, often combining data theft with encryption to maximize pressure on victims. At the same time, attackers are increasingly targeting third-party vendors, turning supply chain security into a top priority.
A global study found that 59 percent of businesses across 14 countries experienced at least one ransomware incident in the past year.
- Zero Trust Security
The traditional model of trusting users and devices within a secure perimeter is no longer viable. Organizations are adopting Zero Trust frameworks that enforce continuous verification, segment networks, and minimize user privileges.
- Quantum risk
While quantum computers capable of breaking current encryption may still be years away, the risk they pose is real. Organizations are beginning to evaluate post-quantum cryptography to safeguard sensitive data from future decryption attempts.
- Privacy regulations
GDPR remains a cornerstone of data protection in the EU, but additional regulations are emerging globally, and reforms are underway to simplify compliance for smaller businesses. This expanding legal landscape is challenging organizations to maintain agility in their compliance efforts.
Turning rules into results: How Dadir helps organizations stay ahead
At Dadir, we believe compliance should strengthen your business, not slow it down. That’s why we focus on making regulatory frameworks like NIS2 and GDPR practical, actionable, and tailored to your environment.
Our multidisciplinary team brings deep expertise in:
- Risk and quality management
- Process design and continuous improvement
We listen, adapt, and build systems that make sense; for your team, your sector, and your goals.
Our services include:
- Risk and readiness assessments based on sector-specific NIS2 & GDPR needs
- Executive briefings and accountability workshops for leadership teams
- Supply chain security assessments and contractual alignment with third parties
- End-to-end cybersecurity program design: policies, reporting, and response
- In-house training and awareness programs that stick
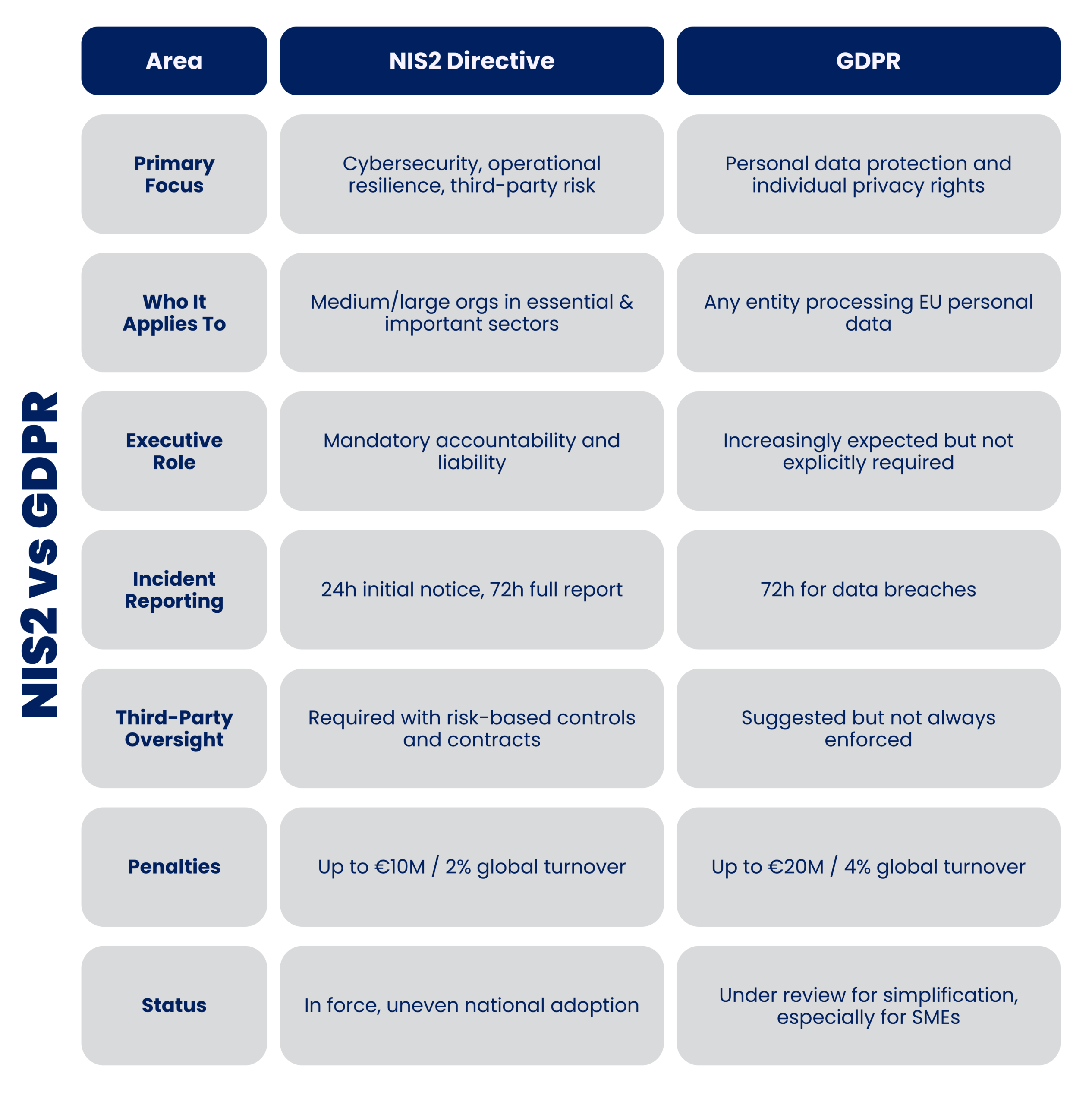
NIS2 vs. GDPR: A side-by-side snapshot for 2025
Understanding the differences and overlaps between NIS2 and GDPR is essential for aligning your compliance strategy. While both frameworks aim to strengthen digital trust and security, their scopes, enforcement mechanisms, and executive responsibilities vary in important ways.
Moving forward: Prepare, don’t react
The convergence of NIS2 and GDPR in 2025 isn’t just about legal compliance—it’s a wake-up call for organizations to embed digital trust, resilience, and accountability into their DNA.
If you’re unsure where to start or need a hands-on partner who speaks both business and regulation, Dadir is here to help.
Conclusion: A new era of strategic compliance
2025 marks more than a regulatory milestone; it’s a turning point in how organizations approach cybersecurity and data protection. NIS2 and the evolving GDPR are not just checkboxes for compliance; they represent a broader shift toward proactive, accountable, and resilient digital operations.
At Dadir, we help translate regulation into real-world application.